Pretexting in cybersecurity is a form of social engineering where an attacker creates a false…


Pretexting in cybersecurity is a form of social engineering where an attacker creates a false…

Cybersecurity is an ever-evolving field crucial in our increasingly digital world. As technology advances, so…

In today’s digital age, where technology is deeply entwined with every aspect of our lives,…

In the evolving landscape of digital technology, the importance of cybersecurity cannot be overstated. Employing…
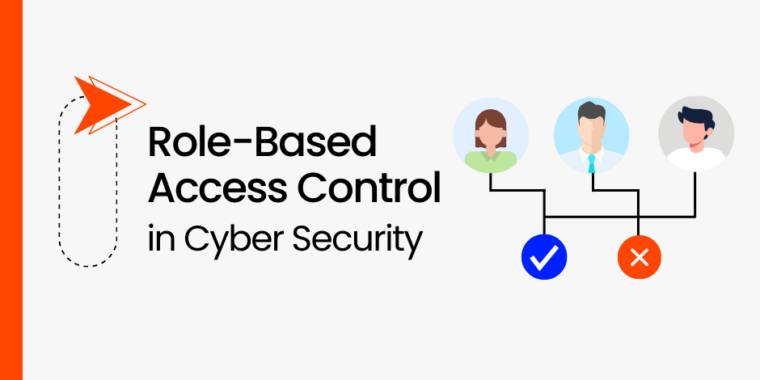
Role-based access control (RBAC) is a critical aspect of cybersecurity that ensures the right individuals…

In the current era of digitization, cybersecurity is a critical concern for both businesses and…

In the field of cybersecurity, you’ll commonly see the terms ‘network-based intrusion detection system’ (NIDS)…
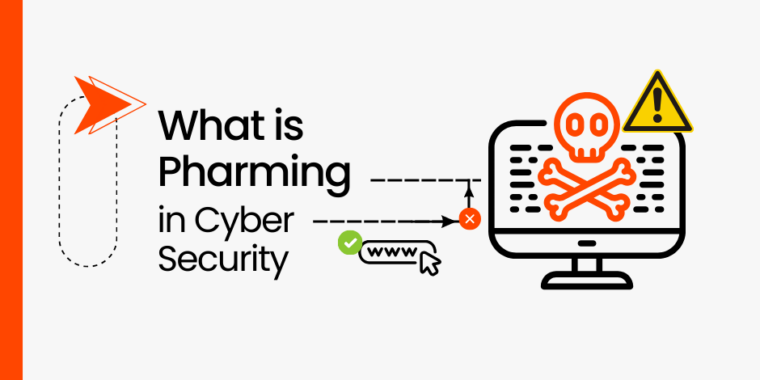
Pharming in cybersecurity is a growing concern. It’s a sophisticated form of online fraud that…

Public Key Infrastructure (PKI) is a critical element in the world of cybersecurity. It is…
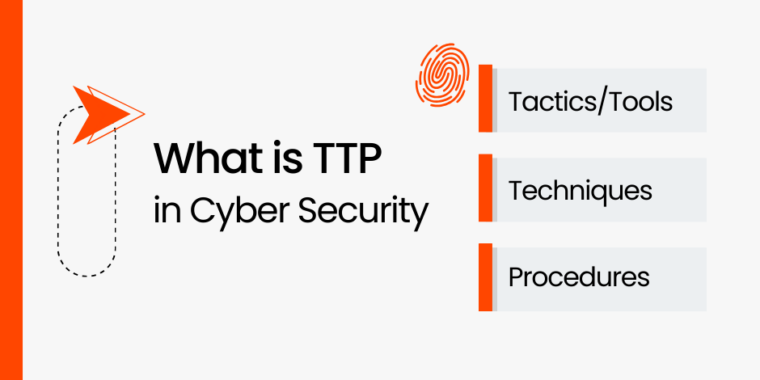
In the ever-evolving realm of cybersecurity, TTP – Tactics, Techniques, and Procedures – has become…